Embark on a journey of knowledge with our information security program initial orientation training answers, meticulously crafted to equip you with the foundational understanding of safeguarding sensitive information. This comprehensive guide unravels the complexities of information security, empowering you to navigate the digital landscape with confidence.
Delve into the intricacies of information security, grasping its fundamental principles, common threats, and essential protective measures. Our expert insights will guide you through security policies, access control mechanisms, data protection techniques, network security protocols, and physical security best practices.
With each step, you’ll gain invaluable knowledge to safeguard your organization’s critical assets from potential breaches.
Program Overview
An information security program is a comprehensive set of policies, procedures, and practices designed to protect an organization’s information assets from unauthorized access, use, disclosure, disruption, modification, or destruction.
The purpose of this training is to provide employees with a basic understanding of the information security program and their role in protecting the organization’s information assets.
The training is designed for all employees who have access to the organization’s information systems.
The training will be delivered in a series of modules, each of which will cover a different aspect of the information security program.
Information Security Fundamentals
Information security is the practice of protecting information from unauthorized access, use, disclosure, disruption, modification, or destruction.
The key components of information security are:
- Confidentiality: Ensuring that information is only accessible to authorized individuals.
- Integrity: Ensuring that information is accurate and complete.
- Availability: Ensuring that information is available to authorized individuals when they need it.
Protecting information assets is important because it can help to prevent financial loss, reputational damage, and legal liability.
Common information security threats and vulnerabilities include:
- Malware: Software that is designed to damage or disrupt computer systems.
- Phishing: A type of social engineering attack that tricks users into giving up their personal information.
- Hacking: The unauthorized access of computer systems.
- Denial of service attacks: Attacks that prevent users from accessing a computer system or network.
Security Policies and Procedures
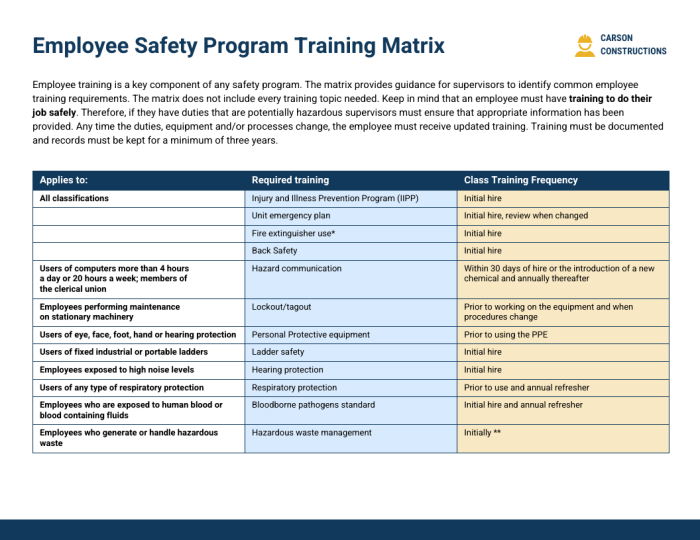
An organization’s information security policies and procedures are a set of rules and guidelines that govern how employees must protect the organization’s information assets.
Employees are responsible for complying with these policies and procedures.
Failure to comply with these policies and procedures can result in disciplinary action.
Employees should report any security incidents to their supervisor immediately.
Access Control and Authentication
Access control is the process of controlling who has access to information and resources.
Authentication is the process of verifying the identity of a user.
There are different types of access control mechanisms, including:
- Role-based access control (RBAC): Grants access to resources based on the user’s role within the organization.
- Attribute-based access control (ABAC): Grants access to resources based on the user’s attributes, such as their job title, location, or department.
- Discretionary access control (DAC): Grants access to resources based on the user’s own discretion.
Strong passwords are essential for protecting access to information and resources.
Employees should create strong passwords that are at least 12 characters long and contain a mix of uppercase and lowercase letters, numbers, and symbols.
Data Protection and Encryption

Data protection is the process of protecting data from unauthorized access, use, disclosure, disruption, modification, or destruction.
Encryption is a process that converts data into a form that cannot be easily understood by unauthorized individuals.
There are different data protection techniques, including:
- Encryption: Converts data into a form that cannot be easily understood by unauthorized individuals.
- Tokenization: Replaces sensitive data with a unique token that can be used to identify the data without revealing its actual value.
- Data masking: Replaces sensitive data with fictitious data.
Employees should protect data in transit and at rest.
Network Security: Information Security Program Initial Orientation Training Answers
Network security is the process of protecting networks from unauthorized access, use, disclosure, disruption, modification, or destruction.
There are different types of network security controls, including:
- Firewalls: Prevent unauthorized access to a network.
- Intrusion detection systems (IDSs): Detect and report unauthorized access to a network.
- Virtual private networks (VPNs): Create a secure connection over a public network.
Employees should protect network devices and data.
Physical Security
Physical security is the process of protecting physical assets from unauthorized access, use, disclosure, disruption, modification, or destruction.
There are different types of physical security controls, including:
- Access control systems: Control access to physical areas.
- Security cameras: Monitor physical areas.
- Security guards: Protect physical assets from unauthorized access.
Employees should protect physical assets from unauthorized access.
Incident Response and Disaster Recovery

Incident response is the process of responding to a security incident.
Disaster recovery is the process of recovering from a disaster.
Incident response and disaster recovery planning are essential for protecting an organization’s information assets.
The steps involved in an incident response process include:
- Identification: Identifying the incident.
- Containment: Containing the incident.
- Eradication: Eradicating the incident.
- Recovery: Recovering from the incident.
Employees should create and implement a disaster recovery plan.
Employee Training and Awareness

Employee training and awareness are essential for protecting an organization’s information assets.
Employees should be trained on the organization’s information security policies and procedures.
Employees should also be aware of the common information security threats and vulnerabilities.
Organizations should develop and implement an effective employee training program.
Popular Questions
What is the primary objective of an information security program?
To protect the confidentiality, integrity, and availability of an organization’s information assets.
Why is employee training crucial for information security?
Employees are often the weakest link in the security chain, so training them to recognize and mitigate threats is essential.
What are some common types of information security threats?
Malware, phishing attacks, data breaches, and unauthorized access are among the most prevalent threats.
How can I create a strong password?
Use a combination of upper and lowercase letters, numbers, and symbols, and avoid common words or personal information.
What are the key components of a disaster recovery plan?
Data backup, system recovery procedures, and communication protocols are essential elements of a comprehensive disaster recovery plan.